
Asset Inventory Service
Find, manage, and analyze your OT inventory
Network monitoring and vulnerability detection help you achieve greater cybersecurity for your OT ecosystem
The Asset Inventory Service improves the cybersecurity of your operational technology (OT) and cooperates with versiondog and all standard automation devices used by your OT ecosystem. The monitoring system contains OT asset identification in the form of an active scan, a network risk analysis as well as the ability to identify vulnerabilities and cyberattacks.

The basis for your smart factory – intelligent protection for your OT
ASSET DETECTION
Automatic asset detection thanks to active scans as well as import of connected devices from versiondog- ASSET MANAGEMENT
Manage the data of all your OT assets even if they are connected or not connected to versiondog
- RISK & VULNERABILITY SCORE
Detailed information about risk levels and vulnerabilities for all of your assets
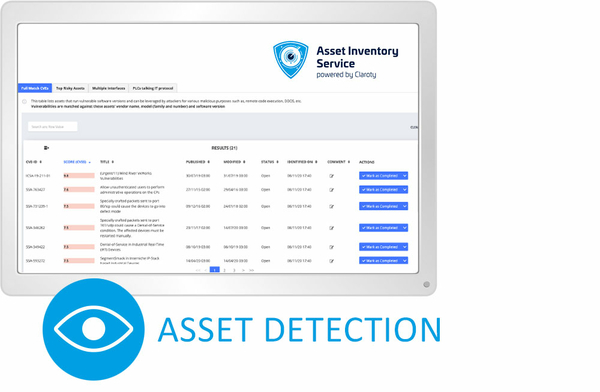
Asset Detection
The devices connected in versiondog are automatically updated and added to the existing list along with all existing information. You can also detect any assets (using the active scan of your network) that are not backed up in versiondog at present and therefore not included in your disaster recovery plan. All identified assets will be automatically added to your central inventory list.
Here’s how you can easily eliminate gaps in your disaster recovery strategy.

Asset Management
Manage all of your critical infrastructure assets automatically in a central inventory list. Thanks to the additional detailed information from versiondog, you will receive a clear and straightforward allocation.
Receive all important information (e.g. firmware versions) concerning your critical assets at a glance.

Risk & Vulnerability Score
Ensure your device data is up-to-date thanks to the latest common vulnerabilities and exposures (CVE) data and gain access to an extensive library of insecure protocols, misconfigurations and other vulnerable security points.
Gain an automatic assessment of all vulnerabilities, affected assets and the entire industrial network.
Reasons why you should incorporate the Asset Inventory Service at your company
![[Translate to English:] Bild mit Lupe für Transparenz](/fileadmin/_processed_/0/7/csm_Transparenz-versiondog-Insights_7b8d6e5055.jpg)
Single Source of Truth
Gain overall device transparency as well as automatic device inventory with comprehensive information about hardware, firmware, model, rack slot, IP, manufacturer, etc.
![[Translate to English:] Symbolgrafik für Disaster Recovery](/fileadmin/_processed_/4/a/csm_asset-inventory-versiondog-disaster-recovery-strategie_762d7b87f1.jpg)
Expanded disaster recovery
Identify additional critical network assets not included in your disaster recovery plan and ensure future backups.
![[Translate to English:] Tachometer und Zahnräder](/fileadmin/_processed_/b/a/csm_asset-inventory-versiondog-high-efficiency_0990ac99c4.jpg)
Increased efficiency
Centralized access, management, and reporting for all assets, including vulnerability and risk assessment.
![[Translate to English:] Wippe mit Kreuz und Dollarzeichen](/fileadmin/_processed_/f/8/csm_asset-inventory-versiondog-reduce-total-costs_b420241640.jpg)
Reduce total operation costs
Increase productivity, process streamlining and avoid human error. Thanks to reduced manual effort and simplified reporting you achieve more time to concentrate on more important matters.
FAQ's
- Hardware
- Firmware
- Model
- Rack slot
- IP
- Manufacturer
- And much more!
Active scan
The active scan is unique in that it uses both well-known IT-based queries and detection methods such as SNMP queries and proprietary queries. The unique OEM method of querying these assets is used to ensure the highest level of security. The Asset Inventory Service has broad protocol coverage and has developed specialized engines to query each OT asset according to its specific model and vendor.
The import process is performed automatically after a change in versiondog (e.g. Check-In of a component or (optionally) after each job execution). Since the import takes place on the versiondog server and after Check-In / job execution, the user’s workflow will not be disturbed.

